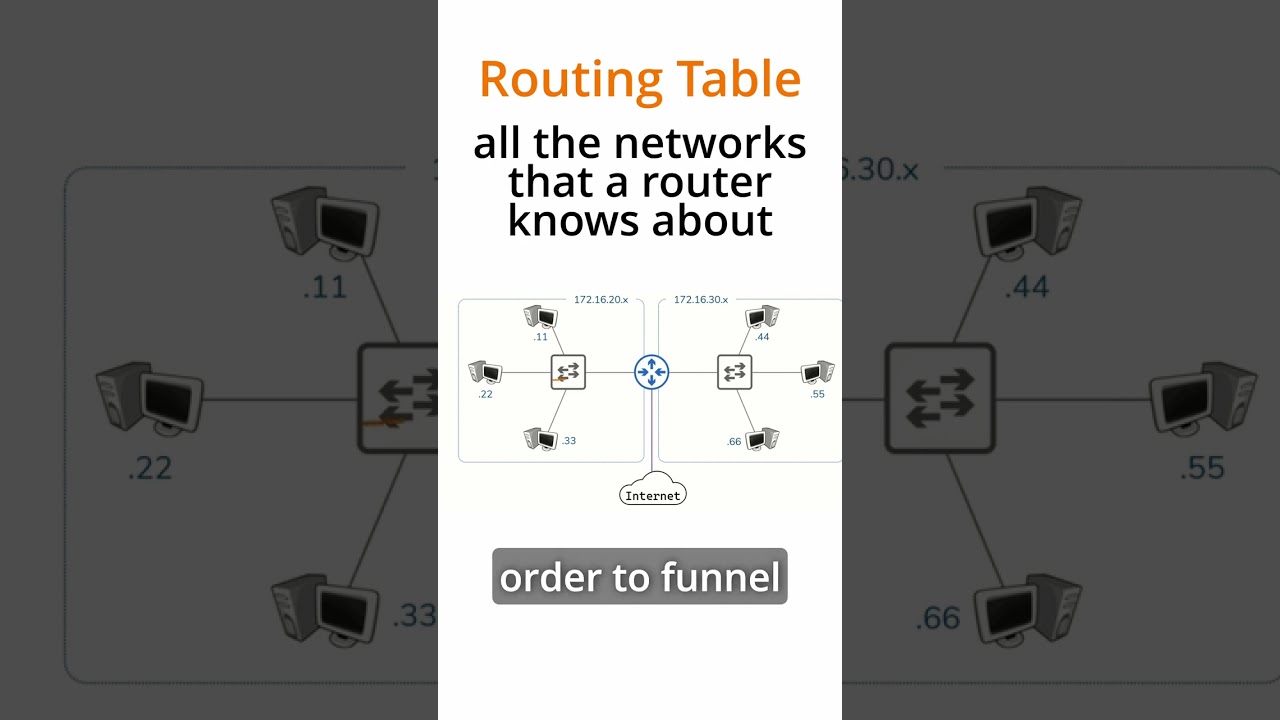
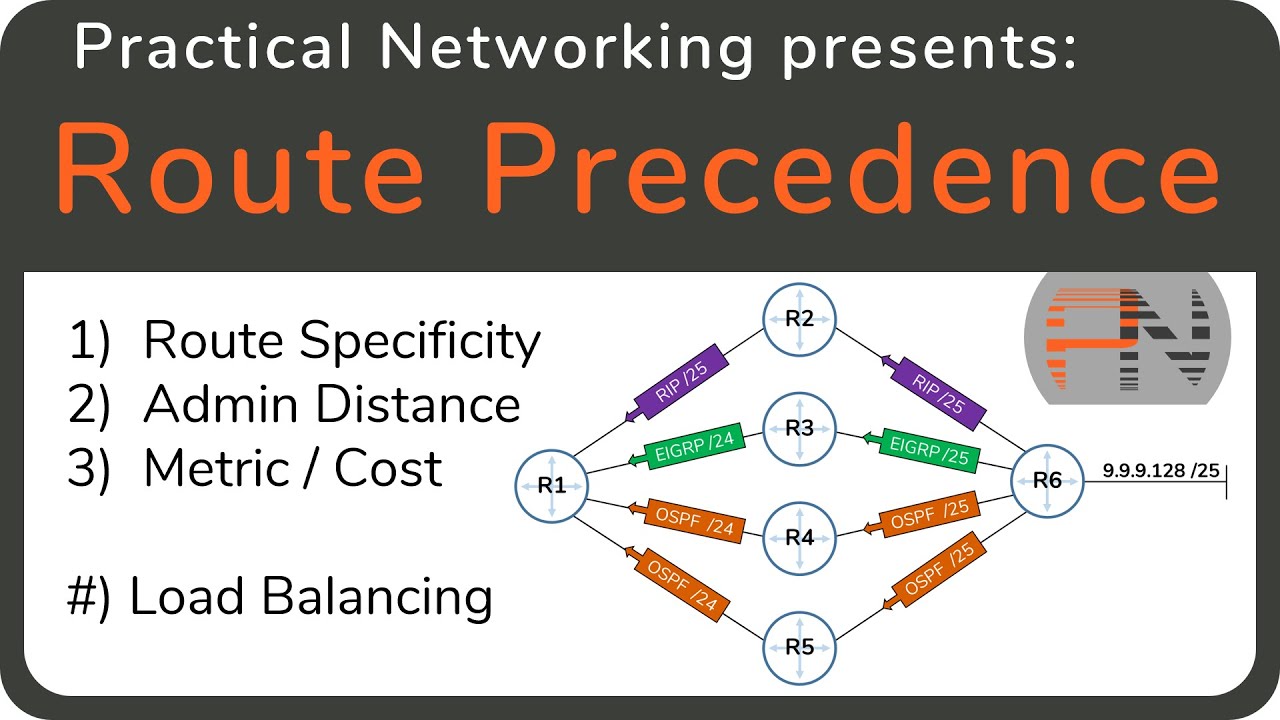
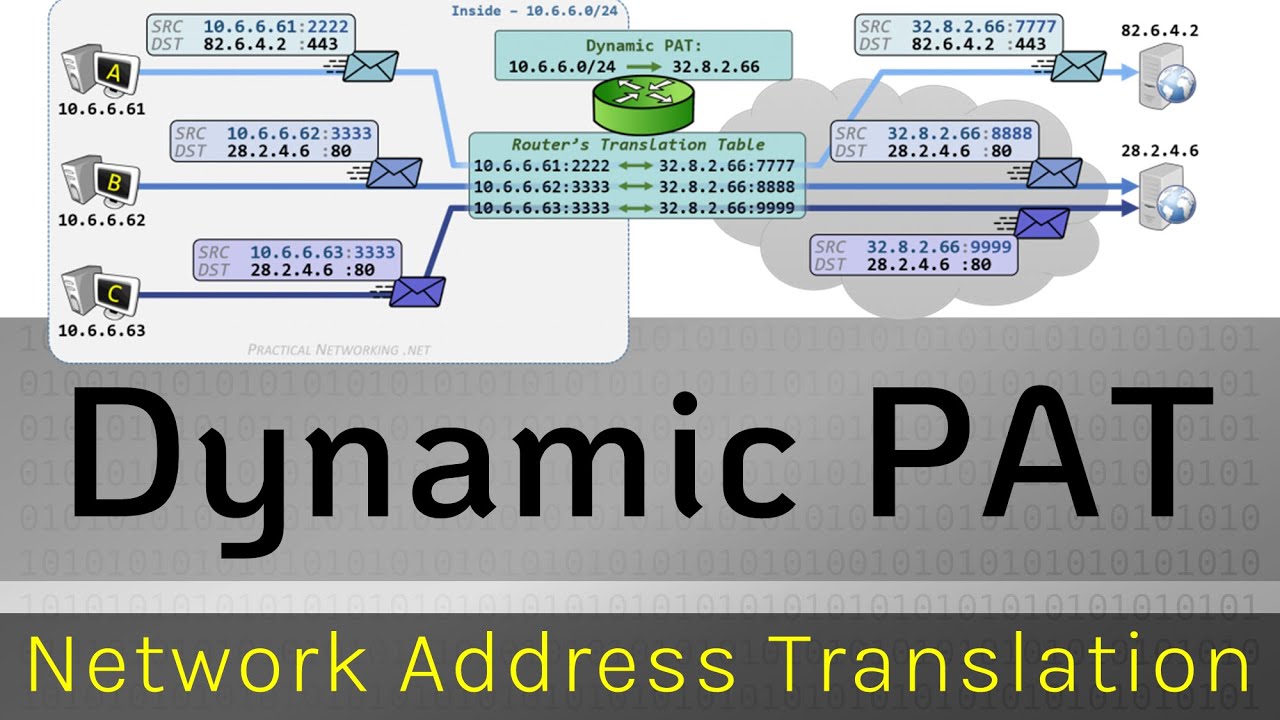
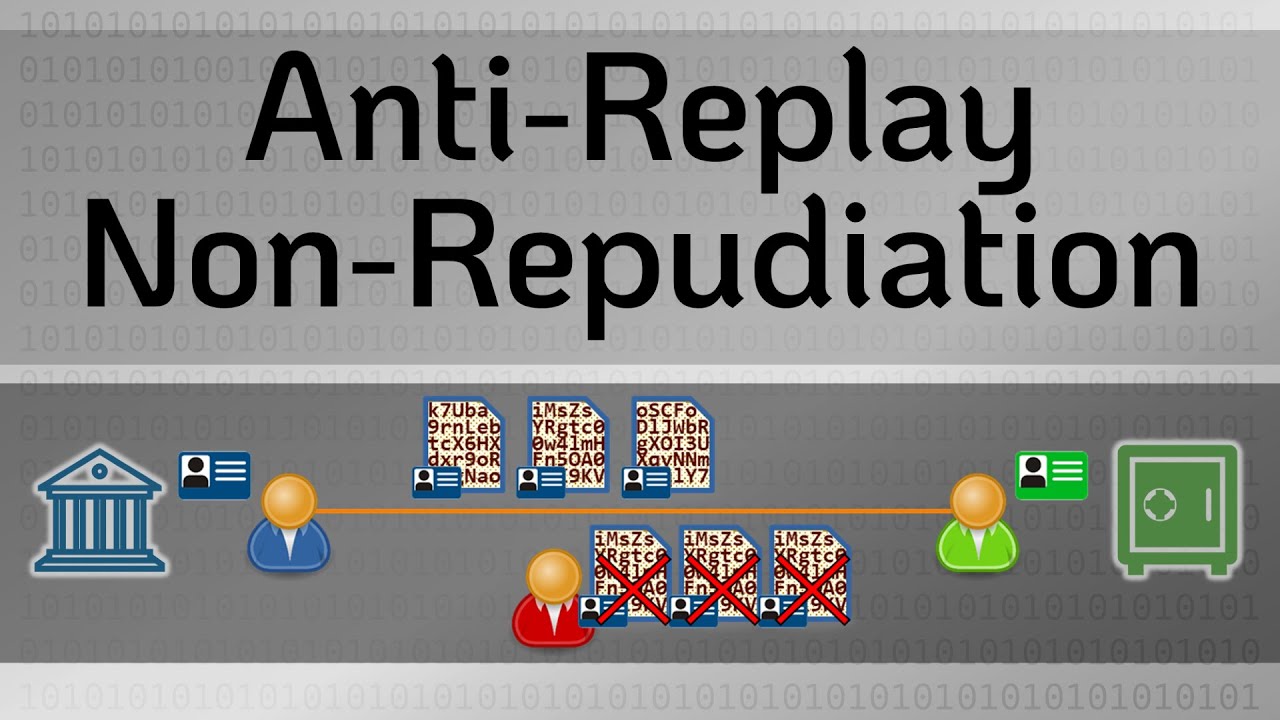
Six More Tips for Maximizing Nexus Switches Performance
Are you working with Nexus switches and looking to enhance your networking experience? Look no further! In this article, we will provide you with six more tips that will surely make your day better. So, let’s dive in! Enable Colorful Interface If you’re tired of the traditional black and white interface, Nexus switches have got … Read more