In the world of technology, encryption and secure connections are essential to protect sensitive information and verify identities. One crucial component that enables this security is the Public Key Infrastructure (PKI). In this article, we will explore the basics of PKI, its key players, and its significance in ensuring confidentiality, integrity, and authentication.
Contents
What is PKI?
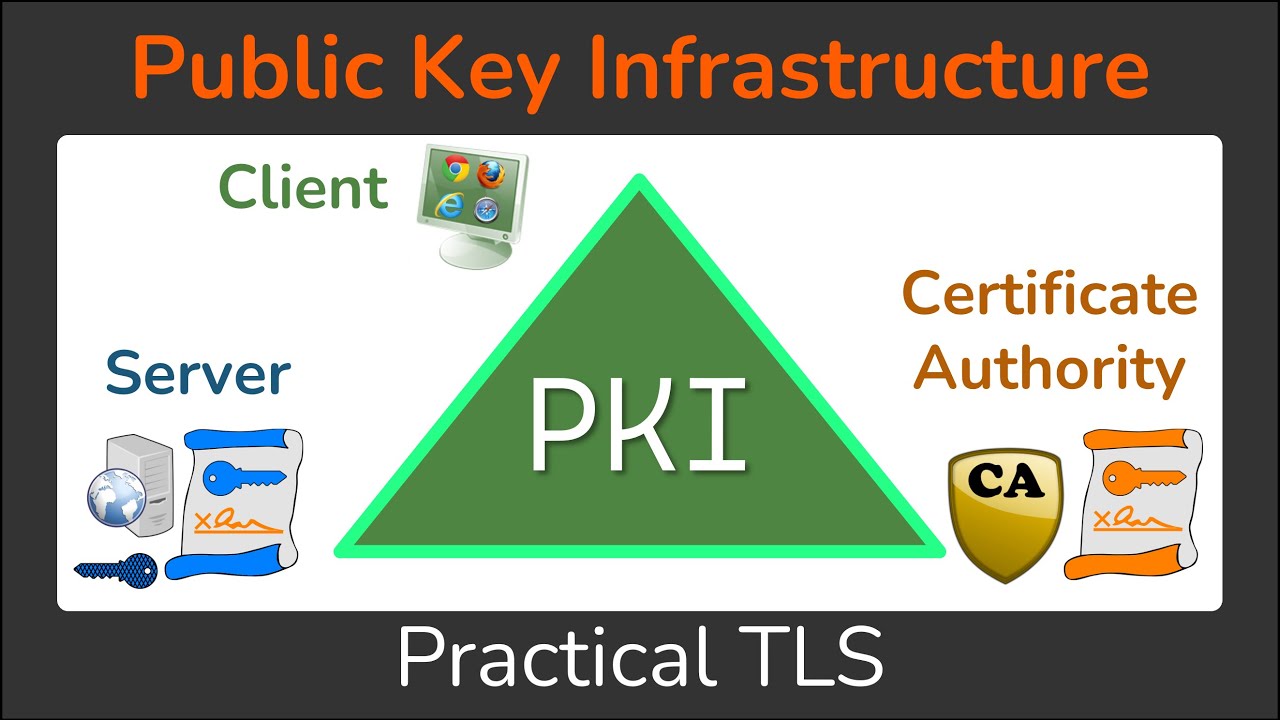
The Public Key Infrastructure (PKI) is a framework that consists of three main entities: the client, the server, and the Certificate Authority (CA). These entities work together to establish secure connections and verify identities.
The Client
The client is an entity that needs to connect securely to something or verify a particular identity. In the context of the World Wide Web, clients are web browsers like Chrome, Firefox, and Safari. They can also include devices that make secure SSL/TLS connections in the Internet of Things (IoT) era.
The Server
The server is an entity that needs to prove its identity. In the web context, servers are the various websites we visit, such as Google.com, bankingwebsite.com, or youremailprovider.com.
The Certificate Authority is the governing entity that verifies identities and issues certificates. In the case of the World Wide Web PKI, there are several well-known public web CAs that sign the majority of certificates. These CAs include Let’s Encrypt, DigiCert, GlobalSign, Sectigo, and Entrust.
The World Wide Web PKI
Most of us are familiar with the PKI used for the World Wide Web. The clients are web browsers, the servers are websites, and the certificate authorities are the public web CAs. These three entities work together to establish secure connections and verify the identities of websites.
Other PKIs
It’s important to note that the World Wide Web PKI is not the only PKI that exists. There are other PKIs tailored for specific purposes, such as code signing. Code signing PKIs involve their own set of entities: the operating system as the client, the software as the server, and a set of code signing CAs to sign and verify the identity of software. These code signing CAs are different from the CAs that sign website certificates.
Additionally, individual organizations can have their own internal corporate PKI. These PKIs are used to secure internal corporate resources, such as HR portals, ticketing systems, scheduling systems, or chat programs. Companies often set up their own internal CAs to sign and create certificates for these resources, enabling their employees to trust them.
FAQs
Q: Why is PKI important?
A: PKI is crucial for establishing secure connections, verifying identities, and ensuring confidentiality, integrity, and authentication.
Q: Can there be multiple PKIs coexisting?
A: Yes, there can be multiple PKIs tailored for different purposes or used within different organizations.
Q: Are all CAs the same?
A: No, there are different CAs that specialize in different types of certificates, such as web certificates or code signing certificates.
Conclusion
Understanding the Public Key Infrastructure (PKI) is essential for anyone interested in cybersecurity and secure connections. The combination of clients, servers, and certificate authorities forms the backbone of PKI, enabling secure communication and identity verification. Whether it’s the World Wide Web PKI or other specialized PKIs, the principles remain the same. To learn more about PKI and SSL/TLS, check out the Techal’s practical TL course—a comprehensive resource for mastering encryption techniques and becoming an SSL expert.

