Have you ever wondered how your data is protected when it is transmitted over the internet? The answer lies in hashing algorithms, a fundamental aspect of cryptography. In this article, we will delve into the world of hashing, understand what it is, and explore its significance in data security.
Contents
What is a Hashing Algorithm?
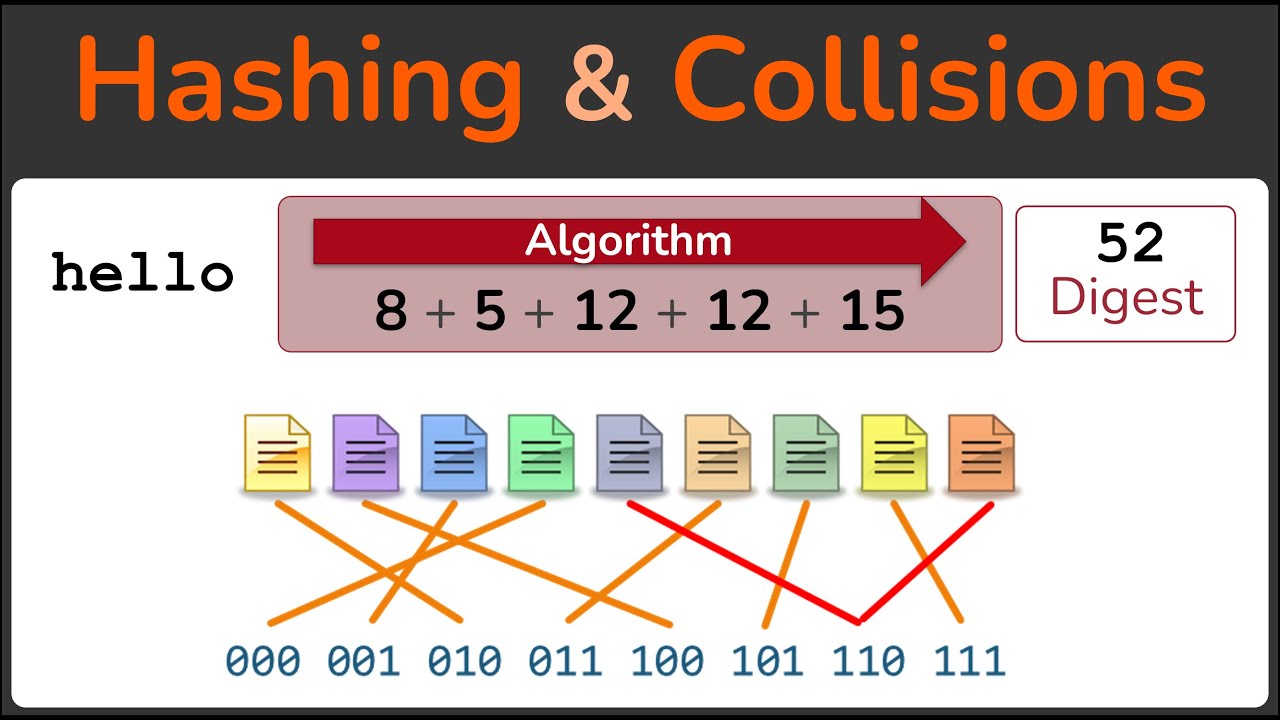
A hashing algorithm is a mathematical formula that takes a message of any length and produces a unique output called a message digest. Think of it as a fingerprint or representational sample of the original message. For example, if we input the word “hello” into a hashing algorithm that simply adds up the letter values (e.g., h=8, e=5, l=12, o=15), the resulting digest would be a unique number, such as 52.
Message Digest and its Purpose
The message digest, also known as a checksum, fingerprint, hash, or CRC, serves a crucial purpose in data security. It enables us to compare two original messages to determine if they are the same or different. For instance, if someone changes the word “hello” to “cello” and we run both words through the same hashing algorithm, the resulting digests would be different (52 and 47, respectively). By comparing these digests, we can easily determine that the original messages are different.
Requirements for a Strong Hashing Algorithm
While our example of adding letter values works as a simple hashing algorithm, real-world algorithms need to meet four essential requirements to be considered secure:
- Infeasibility: It should be infeasible to produce a specific digest. In other words, it should be extremely challenging to find multiple messages that result in the same digest.
- Irreversibility: It should be impossible to extract the original message from its digest. This property ensures that the digest acts as a one-way encryption.
- Small Change, Drastic Difference: A small change in the original message should produce an unrecognizable difference in the resulting digest. This property prevents potential attackers from inferring any information about the original message.
- Fixed-Length Digest: The resulting digest should always be of the same length, regardless of the length of the original message. This property ensures consistency and prevents potential attackers from deducing the original message’s length.
These requirements ensure the integrity and security of the hashing algorithm.
FAQs
Q: Can you provide examples of real-world hashing algorithms?
A: Two commonly used algorithms are MD5 (128-bit) and SHA-1 (160-bit). Additionally, the SHA-2 family consists of algorithms that produce different-length digests to meet various security requirements.
Q: Are collisions avoidable in hashing algorithms?
A: Collisions, where two different messages produce the same digest, are unavoidable due to the limited number of possible digests. However, strong hashing algorithms make collisions extremely rare.
Q: How are hashing algorithms used in data security?
A: Hashing algorithms play a crucial role in data integrity, ensuring that transmitted data remains unaltered. By comparing message digests, recipients can verify if the received message matches the original.
Conclusion
Understanding hashing algorithms is key to comprehending the foundational principles of data security. These algorithms provide a unique fingerprint for messages, allowing us to determine if messages are the same or different. By meeting specific requirements, hashing algorithms guarantee infeasibility, irreversibility, small change and drastic difference, as well as a fixed-length digest. As technology continues to advance, hashing algorithms will play an even more significant role in securing our digital world.
For more insightful articles on technology, visit Techal.



