When it comes to securely exchanging data between clients and servers, there are four crucial elements involved: authentication, symmetric encryption, hashing algorithms, and key exchange protocols. These elements ensure the confidentiality, integrity, and identity verification of the communication. But how do clients and servers agree on the specific protocols to achieve these goals? That’s where cipher suites come in.
A cipher suite is a combination of protocols that define the secure communication between a client and a server. It consists of four elements: a key exchange protocol, an authentication protocol, a symmetric encryption protocol, and a hashing algorithm. Let’s take a closer look at what each of these elements means.

Contents
Key Exchange Protocol
The key exchange protocol provides a way for the client and server to generate the necessary secret keys required for symmetric encryption and message authentication codes (MACs). There are various key exchange protocols available, such as Diffie-Hellman Ephemeral (DHE) and RSA.
Authentication Protocol
The authentication protocol verifies the server’s identity and ensures that the client is communicating with the intended server. Common authentication protocols include RSA and Elliptic Curve Digital Signature Algorithm (ECDSA).
Symmetric Encryption Protocol
The symmetric encryption protocol is responsible for ensuring the confidentiality of the data being transmitted between the client and server. AES (Advanced Encryption Standard) is a widely used symmetric encryption protocol.
Hashing Algorithm
The hashing algorithm is used within a message authentication code (MAC) to verify the integrity of the data. SHA (Secure Hash Algorithm) is commonly used for hashing.
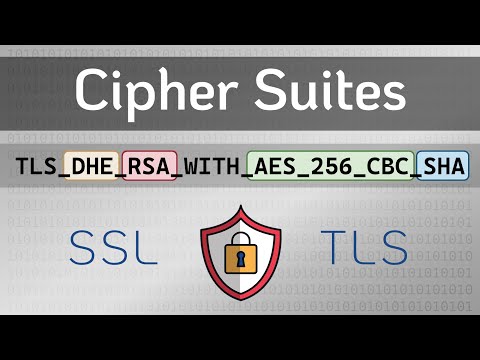
A cipher suite is represented by a long string of letters, with each element corresponding to a specific protocol. For example, DHE_RSA_AES_256_CBC_SHA represents a cipher suite with DHE for key exchange, RSA for authentication, AES-256-CBC for symmetric encryption, and SHA for hashing.
Example of a cipher suite: DHE_RSA_AES_256_CBC_SHA
Cipher suites are not created on the fly but are chosen from a pre-built list maintained by IANA (Internet Assigned Numbers Authority). This list includes numerous cipher suites, each providing different protocols for key exchange, authentication, encryption, and hashing. To see the complete list of cipher suites, visit https://techal.org/.
To better understand the strengths and weaknesses of different cipher suites, let’s explore the most common protocols for each cryptographic function.
FAQs
Q: Can clients and servers create their own cipher suites?
A: No, clients and servers select cipher suites from a pre-built list of options.
Q: Are all cipher suites equally secure?
A: No, the security level varies depending on the protocols used in the cipher suite.
Q: Does TLS 1.3 change the way cipher suites work?
A: Yes, TLS 1.3 introduces changes to cipher suites, which will be discussed in a dedicated module of this course.
Conclusion
Cipher suites play a crucial role in establishing secure communication between clients and servers. By understanding the elements within a cipher suite and the protocols they represent, you can make informed decisions about which cipher suites are strong and secure. Stay tuned for upcoming lessons on key exchanges, authentication protocols, symmetric encryption protocols, and hashing algorithms. With this knowledge, you’ll become better equipped to navigate the world of secure communication.
For more in-depth knowledge about SSL and TLS, check out the comprehensive course “Practical TLS” on Techal. This course covers cryptography, certificates, private keys, the handshake process, and everything you need to become an SSL expert. Don’t miss out on the chance to become proficient in SSL and TLS protocols.